July 24, 2018
A Cloud Migration Framework — Part 3
Following through on the detailed steps described in the roadmap leads to a successful migration to the cloud.

Those of you have read part 1 and part 2 of this blog series already know all about the cloud migration framework — what it is, why it’s important and how to get started.
This post will discuss the last piece of the puzzle: the migration.
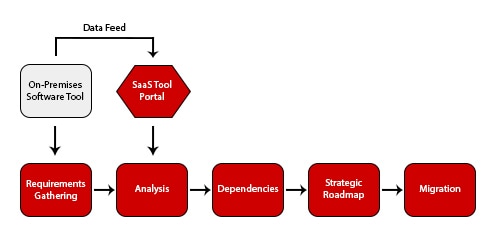
Migration Framework
Key Steps for a Cloud Migration
The actual migration should start in a pilot mode, using your organization’s migration tool of choice. Part of the discussion in planning a strategy around migration includes understanding the approach for moving applications. That is another framework discussion: How to map and use applications and what works and may not work in a cloud environment.
Your organization needs to implement these key practices throughout the entire process of migration:
- Communicate constantly to all stakeholders: Ensure that communications are complete, constant and timely.
- Set up sandboxes or development environments where people can experiment: The migration is a singular process but part of the effort for knowledge transfer involves getting coworkers comfortable with the cloud environment. Setting up a play area where they can experiment, but does not interfere with migration planning and strategy, is an important strategy for team cohesiveness and comfort.
- Organize a cloud strategy team: Identify which coworkers are on the key cloud team.
- Define business goals:. Understanding these goals helps with the architecture of the migration.
- Define technical goals: Understanding the goals of the technical community is necessary in architecting the solution.
- Understand governance (especially data): How governance will work in the cloud, and more important, how data is managed and protected is very important for a successful migration.
- Understand financial impacts: Expectations and understanding of the cost of migrations including future costs and scalability expenses.
- Follow a performance checklist: Develop a checklist on performance requirements, and then verify them after the migration.
- Perform a security gap analysis: Understand their current in-house security needs and how they will change after migration.
The migration should follow the roadmap developed using the wave or grouping concept. This article is not intended to detail the process of implementing the tool used for the actual migration, as different clouds use different methods. No matter what the tool chosen to perform the migration, setup will need to be done in the data center to facilitate the migration. The groupings or waves that have been agreed upon need to be accessed and configured so that the configurations of the virtual machine are carried across to the migration build.
Migration Testing
Testing of the concept is needed to ensure that the design agreed upon actually works as intended. Testing can consist of using JSON templates, or doing a small migration to ensure that the configuration intended is realized as expected in the Infrastructure as a Service (IaaS) cloud environment.
Pilot
A pilot migration should be implemented to test the concepts developed throughout the engagement. Once this is successful and everyone agrees it works as intended, then the step-by-step full migration can begin.
This framework for migration is an overview of the process involved in putting together a cloud migration strategy. If you are new to migrating to a public Infrastructure as a Service cloud, this will help you get started to understand what you need to know. It is no substitute for researching detailed information that dives into areas I touched on, but it can help you get a handle on what you need to know to get started. Once successfully in the cloud, the journey is only beginning!
Start working on your cloud migration with a CDW Cloud Consultation.
