December 21, 2017
Exploring Software-Defined Access (SDA) for Campus Networking
Cisco’s new offering rethinks campus networking and tackles its core challenges.

Over the last few years, we have seen the rise of software-defined WAN (SD-WAN) solutions being deployed with great success in our customer networks. They have realized benefits such as lower TCO due to using commodity internet circuits, enforcement of application SLAs across all transports with added intelligence, and accelerated deployment and troubleshooting via automation and orchestration platforms.
Cisco is now looking to deliver software-defined networking (SDN) to campus local area networks with their new Software-Defined Access solution.
What Is Software-Defined Access?
Software-Defined Access combines various technologies and platforms into a single, advanced solution that changes the way campus networks are deployed.
The solution encompasses the following platforms:
DNA Center Appliance
This is a hardware appliance that runs DNA-Center, the next iteration of APIC-EM, and the Network Data Platform (NDP). These platforms facilitate the automation, orchestration, visibility and troubleshooting of the solution. NDP is an optional, but highly recommended, component of Software-Defined Access.
Identity Services Engine
These hardware or software appliances deliver AAA services to wired and wireless networks, and provide many of the security components of the Software-Defined Access solution. ISE is an integral component of Software-Defined Access.
Fabric Devices
These are network devices (routers, switches, access points, etc.) that support the Software-Defined Access solution.
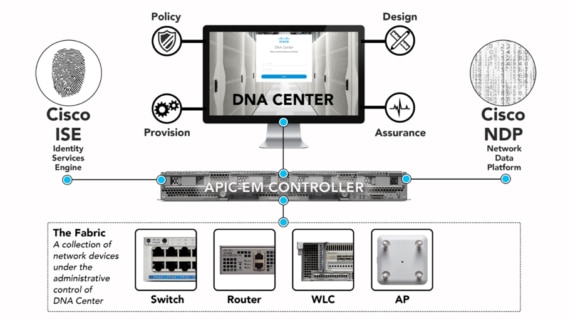
Components of Software-Defined Access SOURCE: Cisco
The solution encompasses the following technologies:
- VXLAN: Used to build an overlay network for the data plane
- LISP: Builds control plane to enable host mobility
- VRF / TrustSec: Security plane of the solution offering macro/micro segmentation
- IS-IS: Used as the underlay routing protocol, building a ECMP routed underlay (Any protocol, such as EIGRP or OSPF, can be used to build the routed underlay, but when you choose IS-IS, DNA-C can automate the deployment of the underlay for you.)
What Problems Does Software-Defined Access Solve?
Campus networks have been designed the same way for the last 20 years. With this solution, Cisco is looking to solve some of the major problems we face in the campus, and shake up the fundamental design.
Software-Defined Access looks to solve the following problems:
1. Security/Segmentation
How it is done today: To create segmentation, customers are doing things like steering all the traffic through firewalls, using VLANs, ACLs, VRF-lite or deploying MPLS. Some customers have deployed TrustSec into their networks, but have found it historically difficult to implement. Security is also difficult and time-consuming to maintain as customers have numerous firewalls interface with thousands of lines of access control lists to limit traffic flows. Today, security at the edge is handled by customers deploying 802.1X and ISE in their networks. We have seen great success among customers adopting and deploying 802.1X, but it can be a timely process to create, test and roll out 802.1X organizationwide.
How it is done with Software-Defined Access: Macro-segmentation is created by Software-Defined Access via VRFs and microsegmentation via Cisco TrustSec, which uses a security group tag (SGT) to map a user’s identity to a tag rather than an IP address. Writing security rules off this tag greatly improves the readability of the security policy, and significantly reduces maintenance; going from thousands of ACL entries to tens of SGT entries. Software-Defined Access also automates the process of deploying 802.1X to the fabric edge. The deployment and maintenance is automated and managed via the DNA-Center appliance and Identity Services Engine.
2. Host Mobility
How it is done today: Today, when a user roams throughout the network, their IP address changes, making it difficult to base security policies on IP addresses and creating complex IP schemes to maintain.
How it is done with Software-Defined Access: Users can seamlessly roam over an L3 network while maintaining the same IP address by using LISP as the control plane protocol. In this solution, security enforcement is achieved using SGTs that render IP addresses much less relevant. With this model, you can use very large IP pools without worrying about broadcast storms or using IP addresses for security enforcement.
3. Automation and Orchestration
How it is done today: Today, customers use many different systems to help automate and orchestrate the deployment of a network. Most of our customers still manually deploy their networks via the CLI, which can take over a week to stand up a site, including: provisioning VRFs, configuring dynamic routing protocols, configuring switching features and configuring 802.1X.
How it is done with Software-Defined Access: The entire Software-Defined Access solution is deployed and managed via Cisco DNA Center, providing customers with a single pane of glass for all network tasks. DNA Center can automate all of the deployment tasks, which would normally take over a week, into a few hours.
4. Network Visibility
How it is done today: Today customers must use third-party tools to try to gain visibility into their network, but still generally lack meaningful, actionable data. If a user calls into a customer’s help desk, gaining visibility into historical network issues is near impossible, making troubleshooting a difficult and time-consuming task.
How it is done with Software-Defined Access: Cisco’s Network Data Platform (NDP), an optional component of the Software-Defined Access solution, delivers end-to-end visibility, analytics and troubleshooting tools. With NDP, a help desk employee can get a 360-degree view of client and devices historical experience on the network. NDP can show issues and trends related to things like device onboarding, app experience and more. For example, NDP could identity a wireless issue in the network that correlates to the user’s ticket to quickly identify and resolve the ticket.
What Next Steps Should I Take?
Cisco’s Software-Defined Access solution is one piece of Cisco’s holistic DNA architecture for the network, and it is in its inception. CDW recommends that customers spend time learning about the solution, preparing their networks, and getting the solution into their lab environments while giving the solution time to mature.
Take the following steps to prepare yourself for Software-Defined Access and a DNA-ready network:
- Upgrade network hardware to platforms that support the new architecture. This refers primarily to the Catalyst 9000 Series switches.
- Maximize the ISE footprint in your network. ISE is a major component of the SD-Access solution.
- Pilot DNA-C and SD-Access in a lab environment to become familiar with the technologies that make up the solution.
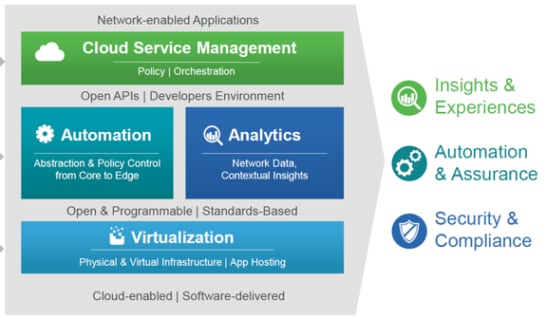
Cisco’s DNA architecture SOURCE: Cisco
You can learn more about Software-Defined Access and see the supported platforms by exploring Cisco’s Software-Defined Access Landing page.
You can also check out Networktest.com’s recent assessment of Software-Defined Access.
Learn more about CDW’s networking solutions, services and partnerships.
